Foil Auth
Secure OTP (One-Time Password) generator for Sailfish OS.
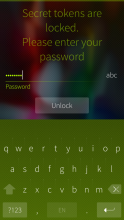
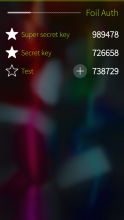
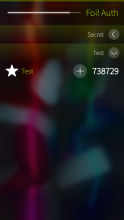
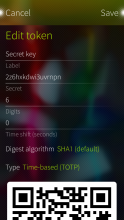
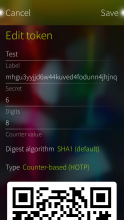
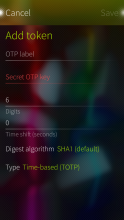
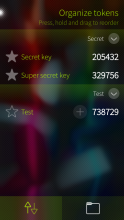
Foil Auth keeps secret authentication keys encrypted with your Foil password. Supports time-based (TOTP), counter-based (HOTP) and Steam passwords. Tokens can be shared and imported via QR codes.
Foil password (and the RSA encryption key ~/.local/share/foil/foil.key) is shared with Foil Pics and Foil Notes. Encrypted authentication keys for OTP generation are stored in ~/Documents/FoilAuth.
The format of the encrypted file is described here.
Note that you can add your encrypted files and the Foil key to the backup with the help of My Backup app.
Source code: https://github.com/monich/harbour-foilauth
Category:
Keywords:
Application versions:
Changelog:
- 1.1.12 (Sep 23 2025)
- Made organize page headers scrollable
- Fixed wakeup criteria for auto-lock
- Improved Base32 handling
- Freshened up Foil UI - 1.1.10 (Oct 10 2024)
- Do not run the countdown timer at startup
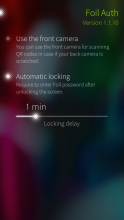
- Added UI for configuring auto-lock delay
- Use wakeup timer for auto-lock
- Allow to scan QR code with the front camera - 1.1.9 (Jul 22 2023)
- Fixed countdown timer on the cover page - 1.1.8 (Jul 22 2023)
- Actually use timeshift
- Fixed couple of Steam token issues - 1.1.7 (May 7 2023)
- Added support for Steam variant of TOTP - 1.1.6 (Apr 14 2023)
- Improved QR code scanning
- Slightly redesigned QR code page
- Request focus for password field at startup
- Updated Swedish translation (Åke Engelbrektson) - 1.1.5 (Jan 15 2023)
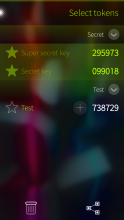
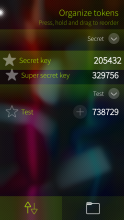
- Support for token groups
- New UI for reordering tokens
- Updated Polish translation (Atlochowski) - 1.1.4 (Sep 26 2022)
- Fixed a problem with import via QR code - 1.1.3 (Aug 17 2022)
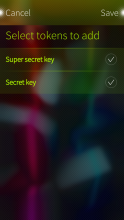
- Implemented import of multiple tokens
- Freshened up the UI
- Removed MD5 support - 1.1.2 (Jul 25 2022)
- Tweaked token creation workflow
- Switched QR-code decoding from zxing to zbar
- Properly support non-ASCII labels - 1.1.1 (Jun 13 2022)
- Allow to turn autolock off - 1.1.0 (Mar 20 2022)
- Opt out of sandboxing (no more Jolla Store updates!)
- Improved QR code scanning performance
- Minor UI tweaks
- Added Chum metadata - 1.0.21 (Nov 15 2021)
- Load libcrypto.so dynamically - 1.0.20 (Nov 5 2021)
- Link OpenSSL 1.0 statically for compatibility with Sailfish OS 4.3
- Updated Polish translation (Atlochowski)
- Tweaked selection page - 1.0.19 (Oct 10 2021)
- Support for HOTP (counter-based) passwords
- Copy password to clipboard on tap - 1.0.18 (Jul 30 2021)
- Allow to choose HMAC digest algorithm
- Generate QR codes with lower error correction level
- Reworked QR code scan UI transitions
- Don't ignore issuer of scanned tokens
- Export or delete multiple tokens at once - 1.0.17 (Apr 18 2021)
- Support for reading otpauth-migration QR-codes - 1.0.16 (Feb 23 2021)
- Hungarian translation (@1Zgp) - 1.0.15 (Jan 9 2021)
- Tweaked remorse items a bit
- Integration with My Backup - 1.0.14 (Dec 20 2020)
- Fixed flashlight - 1.0.13 (Dec 11 2020)
- Fixed QR code scanning on Sailfish OS 4.0
- Updated libqrencode to v4.1.1 - 1.0.12 (Nov 30 2020)
- Added "Show QR code" context menu item
- Display QR code full screen when it's tapped - 1.0.11 (Nov 16 2020)
- Updated Polish translation (Atlochowski) - 1.0.10 (Nov 15 2020)
- Adapted to recent changes in Sailfish OS
- Polished landscape layouts - 1.0.9 (Oct 12 2020)
- Fixed a problem with initial update of current passwords
- More dialog titles - 1.0.8 (Oct 7 2020)
- Added German translation (Samuel Kron)
- Use stronger SHA256 digest for signature
- Tweaked password change UI - 1.0.7 (Jan 3 2020)
- Support for scanning inverted QR codes
- Autolock is delayed by 15 seconds
- Miscellaneous UI tweaks - 1.0.6 (Nov 12 2019)
- Freshened up the UI - 1.0.5 (Apr 22 2019)
- Query the actual maximum zoom from the camera
- Improved French (Quentí) and Polish (Atlochowski) translations - 1.0.4 (Apr 12 2019)
- French translation (Quentí) - 1.0.3 (Apr 11 2019)
- Swedish translation (Åke Engelbrektson) - 1.0.2 (Apr 11 2019)
- Chinese translation (@dashinfantry) - 1.0.1 (Apr 10 2019)
- Polish translation (Atlochowski) - 1.0.0 (Apr 10 2019)
- Initial version






Comments
slava
Fri, 2019/11/29 - 18:36
Permalink
You mean counter-based OTP? That shouldn't be too hard, I just wasn't sure if anyone is using that.
As for backup/export, yes you need both
~/Documents/FoilAuthdirectory and~/.local/share/foil/foil.keyfile - the latter is the RSA private key required for decrypting your tokens (the key itself being AES-encrypted with your password)MacGyver
Sat, 2019/11/30 - 05:46
Permalink
Actually, I might need to recheck, if HOTP is used anymore, I guess TOTP has surpassed it these days.
And thanks for the backup info, now I can sleep knowing my tokens are safely backed up, and encrypted.
Surprisingly few authentication apps have own password as added security layer. I guess most people think it more of a hassle...
slava
Sat, 2019/11/30 - 15:11
Permalink
I'll tell you more :) If you build foilmsg tool then you can decrypt your auth tokens on your computer, you don't need a phone for that. Suppose you have pulled a file named
5E6FD647B7683FACfrom your~Documents/FoilAuthdirectory. Andfoil.keyfile too, of course. Then you can do something like this:where
foil.keyis your foil private key file,xxxxxxxxis your foil password. Your secret token is written to the file namedsecretin the binary form, i.e. as a sequence of raw bytes - in order to get the token string the way you see it in FoilAuth app, you would have to run your secret bytes through a Base32 encoder.kaulian
Thu, 2023/10/12 - 23:46
Permalink
hi @slava,
thanks for tools, i just break my sailfish phone..
I have backup i use your tool to generate the secret file but i cant decode it to view the secret to generate the otp. :/
Could you provide me an example to view secret ?
Thanks
kaulian
Thu, 2023/10/12 - 23:50
Permalink
OK...
Simply base32 secretfile... I searched too complex
MacGyver
Sat, 2019/11/30 - 18:31
Permalink
Interesting, so you could easily move your tokens to other apps too using this method, if needed? Anything can happen, gotta be prepared :)
slava
Fri, 2023/10/13 - 23:46
Permalink
To copy a token from Foil Auth to pretty much any other OTP app you can long-press the token, choose "Show QR code" from the context menu and scan that QR code.
Alternatively, you can choose "Select" from the main pull-down menu, select the tokens you want to copy and tap the Export button in the bottom right corner of the screen. This way you can export multiple tokens at once, at least to Google Authenticator (or any other app which happens to support those multi-token QR codes).
24mu13
Sun, 2019/11/17 - 20:12
Permalink
Interesting thinking about fingerprint authentication: I'm still convinced it's useful and convenient, anyway. What about to have both for instance? Password first time, fingerprint for kind of quick unlock?
nobodyinperson
Sat, 2019/10/12 - 13:29
Permalink
This is a really neat app!
TheJullus
Mon, 2019/09/02 - 18:32
Permalink
Would it be possible to make an option to use fingerprint authtentication for unlocking these foil apps? (Possible in sense of being able to do it and also if it's against the security idea you have (as in "password stronger that PIN code"))
slava
Mon, 2019/09/02 - 19:01
Permalink
Hehe, I was actually considering something like that but it turned out to be impractical and in many ways less secure. Probably the best argument which I heard against that or any kind of biometric authentication in general - "you can change your password but you can't change your fingerprint". When it comes to the actual implementation, it turns out that on most systems you don't have access to raw fingerprint images. You can only match the current fingerprint against the training set and that's it. It's just not enough to generate any kind of hash or anything that could be used as an encryption key.
TheJullus
Mon, 2019/08/05 - 10:58
Permalink
Is it some how possible to use old codes after resetting the phone? I tried to use this app with same password but it says there is no codes (or notes in FoilNotes) Ps. Would it be possible to use fingerprint authentication to open the Foil apps?
slava
Tue, 2019/08/06 - 20:39
Permalink
I'm afraid you've lost your auth token forever and need to request a new one :/ Once the old encryption key is gone, there's no way to recover encrypted data. At least there sholdn't be by design, unless the design is flawed (I hope not).
TheJullus
Thu, 2019/08/08 - 18:53
Permalink
I do have the auth token because I did a backup of my nemo folder. I just switched foil.key in .../nemo/.local/share/foil and it works just fine!!
slava
Thu, 2019/08/08 - 19:48
Permalink
Good! Just don't lose your key and don't forget your password :)
glanternier
Mon, 2019/07/08 - 16:42
Permalink
Ok. I now understand how it works. I had to use inWebo anyway because the helpdesk was being stupid and rigid about this, but I understand what I have to do next time if I want to use the native app. Thanks !!!
glanternier
Sat, 2019/07/06 - 12:32
Permalink
Hello, I want to use Foil OTP to register my O365 account at work, but the IT helpdesk insists on going with an Android app called inWebo. I think that I could use Foil OTP instead, but I don't understand how OTP works technically so I am not sure. The helpdesk will not help me of course. Seeing an non Android / iOS device almost caused them a panic attack :-(
slava
Mon, 2019/07/08 - 17:59
Permalink
If you enter your foil password, select "Add Token" from the pulley menu and press "Scan QR code" button (they provided you the QR code, didn't they?), you should be able to import the token and use Foil Auth for authentication.
These "one time passwords" are essentially one long password (the
secret=part ofotpauth://URL), out of which a shorter one is generated based on the current time. The algorithm implemented by Foil Auth is described heredirec85
Fri, 2019/05/24 - 23:27
Permalink
Works well, great app!
explit
Thu, 2019/04/11 - 00:45
Permalink
Absolut great like all your apps, Slava!
minitreintje
Wed, 2019/04/10 - 15:51
Permalink
The Foil apps are simple, polished and work really well! Thanks Slava!
Historyscholar
Wed, 2019/04/10 - 15:49
Permalink
Nice
Pages